Public-key Encryption Is Based On A Quizlet
Encryption key public usb works oracle drive figure flash explained software lock gif server need do drives ophtek docs cd Encryption key asymmetric public rsa cryptography bob secret message using users decrypt Encryption asymmetric examples alice
Comparison between public key encryption (PKE) and attribute-based
Javatpoint encryption symmetric Difference between public key and private key in cryptography A quick guide to encrypted messaging
How does public key encryption work?
Encryption cryptography basics springboardEncryption key public asymmetric gif tips example Comparison between public key encryption (pke) and attribute-basedEncryption decrypt encrypts.
Cryptography cryptanalysis cryptographic decryption algorithms ciphersEncryption sender identify decryption authentication mailtrap sent explained asymmetric generating Cryptography basics: ins and outs of encryptionKey encryption (sun directory server enterprise edition 7.0 reference).

Difference between public key and private key
I am calvinPublic key cryptography examples : encryption: types of secure Cryptography encryptionEncryption infographic messaging secure encrypted cyberwarfare cybersecurity.
Public key encryptionKey public cryptography encryption scheme decryption most illustration Email encryption: all-in-one guidePublic key encryption.

Encryption attribute pke abe
[tips] public key encryptionKey private public between difference cryptography comparison pediaa Key public encryption private algorithm geeksforgeeks message generation onlyPublic key encryption.
Public and private encryption keysEncryption educba .


Public and private encryption keys | PreVeil

Public Key Cryptography Examples : Encryption: types of secure

Difference Between Public Key and Private Key in Cryptography - Pediaa.Com

Difference between public key and private key - javatpoint
Comparison between public key encryption (PKE) and attribute-based

Public Key Encryption
![[Tips] Public Key Encryption - Asymmetric Key Encryption - Webzone](https://4.bp.blogspot.com/-2-SqJkfOKrQ/W2huVJLI1lI/AAAAAAAADW0/E8-x00Gnjl0bd6lCCxOVUPJKUn97M78_QCLcBGAs/s1600/public_key_encryption.gif)
[Tips] Public Key Encryption - Asymmetric Key Encryption - Webzone
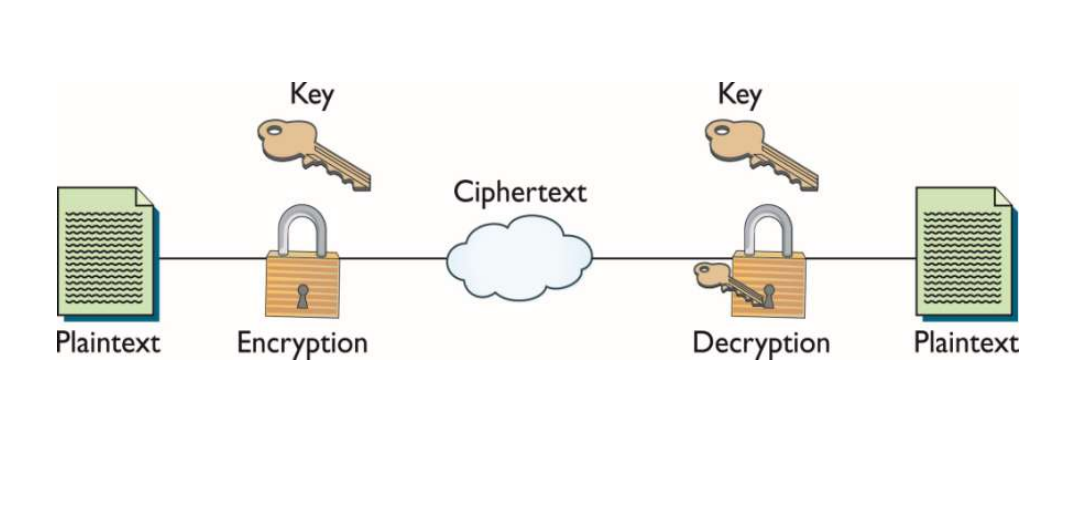
Cryptography-Introduction - 5OBIT

Cryptography Basics: Ins and Outs of Encryption | Springboard Blog
